Detecting Man-In-Middle And Sniffers In The Network
Man-In-The-Middle:
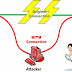
The classic Man-in-the-Middle attack relies on convincing two hosts that the computer in the middle is the other host.This can be accomplished with a domain name spoof if the system is using DNS to identify the other host or address resolution protocol(ARP) spoofing on the LAN.Man-In-The-Middle(MITM) attack is one of the primary techniques in computer based hacking.MITM attack can successfully invoke attacks such as Denial of service, DNS spoofing and Port stealing.
MITM can do the things such as, stealing online account user id, password, stealing of local ftp id, or telnet session etc.
Process to Detecting Man-In-Middle And Sniffers In The Network:
Process-1:
To detect Mitm and sniffers in network the only way is to observe that the connection is equipped with SSL layer.In Practical we should observe the lock symbol in address bar i.e the https connection
If the lock symbol or https is not present in secured server connection such as bank,social networks,etc..., is not present then the connection is in attack. Don't confirm this because we have another test to assure our connection is 100% sniffed
Process-2:
We can detect sniffing in network by using ping command ping the website in command prompt which you think is under sniffing
1)Go to cmd
2)ping the website in command prompt which you think is under sniffing
Ex:ping www.facebook.com
3)It should return the original ip address of the Facebook.
4)If it returns another ip,then the connection is said to be in attack and that ip address is the intruders's ip
That's It.Chao......................!
Ex:ping www.facebook.com
3)It should return the original ip address of the Facebook.
4)If it returns another ip,then the connection is said to be in attack and that ip address is the intruders's ip
That's It.Chao......................!











Hack2B: Detecting Man-In-Middle And Sniffers In The Network >>>>> Download Now
ReplyDelete>>>>> Download Full
Hack2B: Detecting Man-In-Middle And Sniffers In The Network >>>>> Download LINK
>>>>> Download Now
Hack2B: Detecting Man-In-Middle And Sniffers In The Network >>>>> Download Full
>>>>> Download LINK